cybersecurity
Our personal, digital, national and military security depend on a safe cyber space.
AI Race in 2026
By 2026, the global race in Artificial Intelligence (AI) has moved far beyond simple innovation. It has become a strategic competition that shapes economies, national security, education, healthcare, and daily life. Governments, technology giants, startups, and research institutions are all competing to lead in AI development. This race is not only about creating smarter machines, but also about controlling data, setting global standards, and defining how humans and machines will coexist in the future.
By shaoor afridi26 days ago in 01
The Ultimate Guide to Regaining Access to Your Instagram Account. AI-Generated.
Lost access to your Instagram account? Our comprehensive guide covers official recovery methods, security protocols, preventive measures, and answers to all your questions about restoring your Instagram presence.
By Alexander Hoffmann27 days ago in 01
Design Principles Behind High-Trust Digital Wallet Application Solutions
Introduction Digital wallet applications have become a critical component of today’s digital payment ecosystem. From peer-to-peer transfers to online and in-store payments, users rely on eWallet applications to manage sensitive financial transactions securely. As adoption increases, trust has emerged as the most important factor influencing user acceptance and long-term usage.
By Nayel Basim Al Shehhi27 days ago in 01
Healthcare API Penetration Testing: A Practical Guide for Security Teams
Healthcare organizations depend on APIs to connect electronic health records, patient portals, diagnostics platforms, billing systems, and third-party healthcare services. These APIs enable real-time data exchange and operational efficiency, but they also introduce significant security risks if left untested or misconfigured.
By Sam Bishop27 days ago in 01
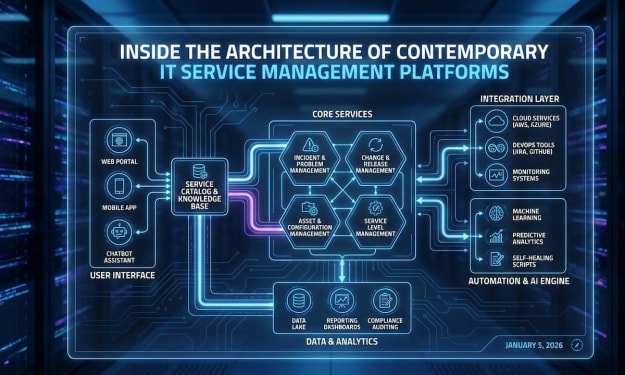
Inside the Architecture of Contemporary IT Service Management Platforms
Introduction As organizations increasingly rely on digital systems to operate efficiently, IT Service Management (ITSM) platforms have become a critical component of modern enterprises. These platforms help manage IT services, streamline workflows, and ensure consistent service delivery. Behind every effective ITSM solution lies a carefully designed architecture that integrates multiple technologies, processes, and systems.
By Nayel Basim Al Shehhi28 days ago in 01
Why Everyone Feels Burned Out in the Age of Hustle Culture
It’s 10 p.m., your laptop is still open, and you’re scrolling through work emails, social media, and half-finished projects. You tell yourself: “Just one more task.” But deep down, you know this isn’t sustainable. Welcome to the age of hustle culture — a world where being busy has become a badge of honor, and burnout is almost expected.
By Yasir khanabout a month ago in 01
How Technology Is Shaping Modern Dating Applications
Introduction Dating applications have transformed how people connect and build relationships in the digital age. What started as simple profile-based platforms has evolved into sophisticated systems powered by advanced technology. Modern dating apps now focus on user experience, security, personalization, and scalability to meet growing user expectations.
By Nayel Basim Al Shehhiabout a month ago in 01
What Is a Security Operations Center (SOC) and Why Businesses Are Moving to Managed SOC Services
In today’s highly connected digital world, cybersecurity is no longer just an IT concern—it is a core business priority. Organizations rely on digital systems for daily operations, customer communication, financial transactions, and data storage. As businesses grow more dependent on technology, cyber threats grow more frequent, more complex, and more damaging. This has led many organisations, especially those operating in fast-paced markets like the United Arab Emirates, to rethink how they monitor and protect their digital environments. One of the most effective approaches to modern cybersecurity is the use of a Security Operations Center, commonly known as a SOC.
By Preethu Sonuabout a month ago in 01
How Modern Technologies Power Secure and Scalable Messaging App Development?
Introduction Messaging applications have become a core part of digital communication, enabling real-time conversations across the globe. From personal chats to business collaboration, users expect messaging apps to be fast, secure, and always available. Behind this seamless experience lies a combination of modern technologies designed to ensure security, scalability, and performance.
By Nayel Basim Al Shehhiabout a month ago in 01
The Complete Guide to Snapchat Account Hacking 2026: Understanding Threats and Protection Methods. AI-Generated.
The Reality of Snapchat Account Compromises Snapchat has emerged as one of the most popular social media platforms, particularly among younger demographics. With over 300 million daily active users sharing ephemeral messages, photos, and videos, the security of Snapchat accounts has become a critical concern. This comprehensive guide examines the actual methods used to compromise Snapchat accounts, the tools involved, and most importantly, how to protect your digital presence effectively.
By Alexander Hoffmannabout a month ago in 01
The Complete Guide to Gmail Account Hacking: Threats, Methods, and Ultimate Protection Protocol. AI-Generated.
Gmail is not just an email service—it's the digital key to your online identity. With 1.8 billion active users, Gmail serves as the authentication hub for banking, social media, cloud storage, and countless other critical services. A compromised Gmail account creates a domino effect, jeopardizing every connected account. This comprehensive guide examines the sophisticated methods attackers use to breach Gmail accounts, the tools involved, and provides an exhaustive protection framework to secure your digital gateway.
By Alexander Hoffmannabout a month ago in 01
How to Hack a TikTok Account in 2026? Understanding Hacks and How to Protect Yourself. AI-Generated.
As the platform has surged past 1.8 billion monthly users, it has transformed from a simple video-sharing app into a digital identity hub packed with personal data, financial connections for creators, and immense social influence. This explosion in value has made TikTok a prime target for cybercriminals, leading to a dramatic increase in account takeover incidents. Whether you're a casual user, a growing creator, or a major brand, understanding these threats is the first step toward building an impenetrable digital defense.
By Alexander Hoffmannabout a month ago in 01