degree
Degrees defined: PhD, Master, Bachelor, Associate–all about that expensive piece of paper called your degree.
What is the Internet of Things (IoT) & How Does it Work?
What is now a standard way of connecting devices to the internet and communicating? The term ‘IoT’ has been around for a long time, but it was only until recently that we realized how close we have come to mass production or communication through it. We are all aware there are billions of pieces of communications equipment connected to the internet. These can be cars, phones, printers, watches, microwaves, coffee machines, music players, or TV remote control to name just some examples. All these are available at the click of a button; no longer do you need an engineer.
By Technogibran3 years ago in Education
It’s the End of the World As We Know It
Hilda Doolittle’s poems are works of spirituality within many different religions that crossover and work together to create a whole image of divinity in her work. Poem 35 of The Walls Do Not Fall section of the Trilogy book references the mythology of Egyptian and Greek Pantheons to create a spiritual and religious atmosphere as she questions the world and how we can change ourselves to make it better.
By Miss Ghoul3 years ago in Education
Good Colleges For BCA
BCA as the name says Bachelor’s in Computer Applications is one of the top preferred courses for the youth who are interested in carving their career in the digital field. The world of mobile applications and web applications is expanding day by day and even in the Covid times, we have seen that it was the e-commerce business only that was up and running while everything else was shut down. You may not need any expert opinion on how important or significant BCA course is but yes you must understand that choosing a good college to pursue the BCA degree is really important. Because all the top colleges that offer BCA also offer campus placement. They invite the leading IT companies of India and abroad who visit the campus and handpick the students offering them placement in various work profiles.
By MMDUMULLANA3 years ago in Education
An overview of cyber security data science from a perspective of machine learning
Introduction The information and communication technology (ICT) sector has advanced significantly over the past fifty years and is now pervasive and tightly intertwined with our contemporary society. As a result, the security policymakers have recently shown a great deal of worry over the protection of ICT applications and systems from cyber-attacks. Cyber security is currently a term used to describe the process of defending ICT systems from multiple cyber threats or attacks. The analysis of various cyber-attacks and the development of defense techniques that preserve several qualities described as below are the main issues with cyber security (Alhayani et al., 2021).
By phd Assistance3 years ago in Education
Stereotype Threat
What is Stereotype Threat In any social situation, stereotypes actively affect the way in which individuals view themselves and others. Stereotypes can alter behaviors, success/failure, and even simple social definitions. These alterations lead to an effect called stereotype threat in which negative stereotypes create an expectation about a certain group, and if this group is afraid to confirm the stereotype, then they will do less well in a certain situation such as women with mathematics (Fiske, 2014). In studies on stereotype threat, it was found that individuals from a stigmatized group underperform in situations where their group membership is made salient. These situations include instances where group members must list their race at the beginning of a test, when the test is described as a diagnostic of ability, or by being the only member of the group present in the situation (Fiske, 2014).
By Cobe Wilson3 years ago in Education
Semantic Search Using Natural Language Processing
Introduction Computer-assisted text analysis is known as natural language processing (NLP). An aspect of NLP is the study of how someone uses and understands language. The goal of this is to develop the tools and methods necessary for computer systems to comprehend, change, and perform a wide range of useful tasks using natural language. Researches in NLP are currently focused on creating sophisticated NLP systems that incorporate both the general text and a sizable portion of the ambiguity and unpredictability of a language. Computational linguistics frequently faces problems with speech recognition, word separation, and other concepts. In NLP, it has been usual practise to create statistical approaches for it (Bast et al., 2016).
By Tutors India3 years ago in Education
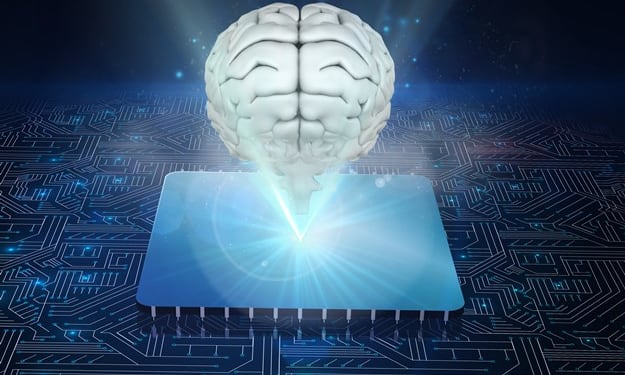
What Is A Neural Network?
The concept of artificial neural networks has always been fascinating and puzzling for the computer science community. It’s a network inspired by living organisms, with the goal of mimicking human intelligence. As it turns out, that is not impossible but there are some limitations to it.
By Technogibran3 years ago in Education
A Beginners Guide on Ethical Hacking Using Kali Linux || What is, How to Install & Use
Kali Linux is an open-source distribution of Linux, which is designed as a cross-platform and can be used on multiple operating systems including Windows, Mac, and various mobile devices. It was developed by Ankur Bhardwaj, who now works as the chief technology officer at Google, in response to high demand from users and developers.
By Technogibran3 years ago in Education
What is Neuromorphic Computing and How Does Neuromorphic Computing Work?
You’ve probably heard of the term “neuroscience” and have probably looked at one or even two papers from your high school biology class. However, we are not here to talk about neurobiology itself — that is a very different kind of science entirely. Rather, this article will focus on the practical aspects (and technical difficulties) of implementing neuromorphic computing — the idea that computers could be engineered to emulate human intelligence. This article is intended for those who desire to learn more about neuromorphic computing. Our understanding of these ideas has evolved since our last post, but we hope to continue to update readers as we progress in our quest to help you with your personal development as an engineer.
By Technogibran3 years ago in Education
10 Peppers Every Spice Lover Needs to Eat at Least Once
10 Peppers Every Spice Lover Needs to Eat at Least Once Ten peppers is just the tip of the iceberg. There are more than 50,000 different varieties of peppers, and pepper growers constantly create new ones. Because capsaicin is present, peppers are sour and spicy; the more capsaicin a pepper contains, the hotter it will be. American pharmacist Wilbur Scoville devised a method to gauge pepper intensity in 1912. A low Scoville number indicates that your pepper is mild, and a high number indicates that your pepper packs a punch. The Scoville scale is still in use today. Without the added zest that a chilli pepper brings, a meal isn't really a meal for many pepper enthusiasts. Peppers are a great source of fibre, folic acid, potassium, vitamins A and C, and they can also improve the taste of boring foods. There are many pepper enthusiasts in the US, and there are just as many websites that cater to their preferences. A mouse click will quickly bring up articles, recipes, and advice on growing peppers. Each pepper has a Scoville rating, as you can see. On this scale, several peppers have a large range; eating some of them is somewhat risky. Be cautious!
By Paul Smith3 years ago in Education
10 Steps to Finding the Right Biology Degree Program for You
It’s an interdisciplinary field that draws on chemistry, physics, mathematics, and computer science to better understand living organisms. Biology degrees can prepare students for careers in medicine, teaching, or research; they also offer a variety of specializations based on your interests and career goals.
By Bryan Smith3 years ago in Education